🐝 The Attack: RVTools Compromised to Deliver Bumblebee Malware

RVTools, commonly used for VMware environment reporting, was exploited to distribute a variant of the Bumblebee malware loader. The compromise was detected when Microsoft Defender flagged a suspicious version.dll file executing from the same directory as the RVTools installer. Further analysis revealed that the installer had been tampered with to include the Bumblebee loader, a malware known for facilitating ransomware operations and post-exploitation frameworks like Cobalt Strike.
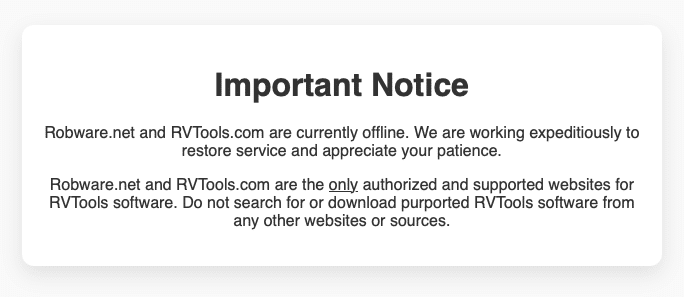
How the Malware Operated
The malicious version.dll file was identified as a custom variant of the Bumblebee loader. This malware is designed to establish initial access within networks, allowing threat actors to deploy additional payloads such as ransomware. In this case, the malware executed stealthily, leveraging legitimate system processes to avoid detection. The use of a trusted tool like RVTools made the attack particularly insidious, as it exploited the inherent trust users place in well-known software.
Implications for Software Asset Management
For organizations relying on SAM tools, this incident serves as a stark reminder of the vulnerabilities within software supply chains. Even reputable tools can be compromised, leading to significant security breaches. It’s imperative for organizations to implement robust security measures, including:
- Verification of Software Sources: Always download software from official, verified sources.
- Regular Security Audits: Conduct periodic audits of all software tools to detect any unauthorized modifications.
- Employee Training: Educate staff on the risks of downloading software from unverified sources and the importance of reporting suspicious activities.
Supply Chain Attacks on the Rise
This incident is part of a broader trend of supply chain attacks targeting trusted software tools. Threat actors are increasingly exploiting the trust users place in legitimate software to distribute malware. The resurgence of Bumblebee malware, despite previous law enforcement disruptions, indicates a persistent and evolving threat landscape .
Recommendations
To mitigate the risks associated with such attacks, organizations should:
- Implement Strict Access Controls: Limit the installation of software to authorized personnel.
- Utilize Advanced Threat Detection Tools: Deploy tools capable of detecting anomalous behaviors indicative of malware activity.
- Maintain an Updated Software Inventory: Keep an accurate and up-to-date inventory of all software assets to quickly identify unauthorized additions.
- Engage in Continuous Monitoring: Establish continuous monitoring protocols to detect and respond to threats in real-time.
The compromise of RVTools to deliver Bumblebee malware highlights the critical need for heightened vigilance in software supply chain security. Organizations must adopt comprehensive security strategies to protect against such sophisticated attacks. By implementing robust security measures and fostering a culture of cybersecurity awareness, organizations can better safeguard their digital assets against emerging threats.









