Oracle’s attempt to hide severe cybersecurity incidents from customers in Oracle SaaS service

Oracle Faces Backlash Over Handling of Cloud Security Breach
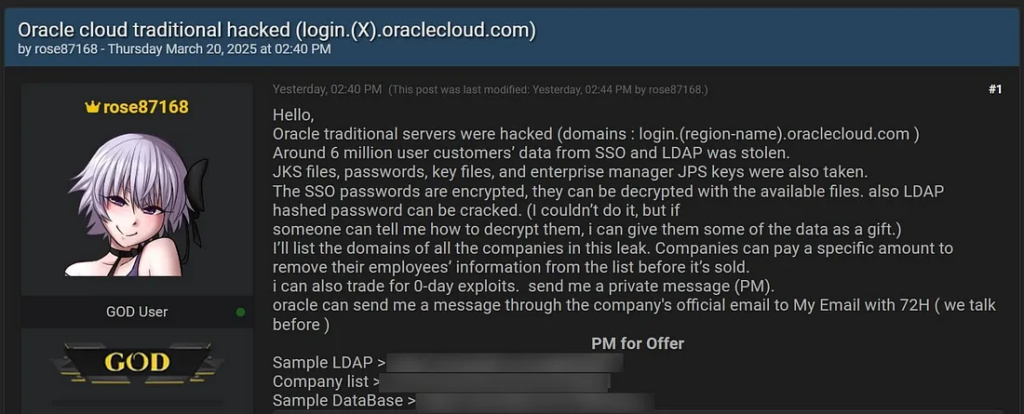
In March 2025, Oracle Corporation found itself at the center of a cybersecurity controversy following allegations of a significant data breach affecting its cloud services. A threat actor, known by the alias “rose87168,” claimed responsibility for infiltrating Oracle’s systems and exfiltrating sensitive data, including six million authentication records. Despite mounting evidence, Oracle’s response has been characterized by denial and obfuscation, leading to criticism from cybersecurity experts and affected clients.
The Breach Unveiled
On March 21, 2025, reports emerged of a threat actor offering for sale a trove of data purportedly stolen from Oracle’s cloud infrastructure. The compromised information reportedly included usernames, email addresses, hashed passwords, and sensitive authentication credentials such as Single Sign-On (SSO) and Lightweight Directory Access Protocol (LDAP) information. The attacker also claimed to have accessed Java Key Store (JKS) files and Enterprise Manager JPS keys, indicating a deep penetration into Oracle’s systems.
Security researchers from CloudSEK suggested that the breach may have exploited a known vulnerability in Oracle Access Manager (CVE-2021-35587), allowing unauthorized access to the company’s login servers. The compromised server, identified as login.us2.oraclecloud.com, was reportedly running outdated software components, making it susceptible to such attacks.
Oracle’s Denial and Wordplay
In response to the allegations, Oracle issued statements denying any breach of its Oracle Cloud Infrastructure (OCI), asserting that “no Oracle Cloud customers experienced a breach or lost any data”. However, cybersecurity expert Kevin Beaumont criticized Oracle’s use of “very specific words” to avoid responsibility, noting that the company rebranded its older cloud services as “Oracle Classic” and claimed the breach only affected these legacy systems.
Further scrutiny revealed that Oracle requested the Internet Archive to delete pages that the threat actor claimed were evidence of the intrusion. Additionally, the threat actor released a recording of an internal Oracle meeting discussing security issues, adding credibility to their claims.
Client Confirmation and Ongoing Concerns
Despite Oracle’s public denials, multiple clients confirmed the authenticity of the leaked data. BleepingComputer reported that companies recognized their own data in the samples provided by the threat actor, including staff email addresses and domain information. Cybersecurity firm Grip Security also noted that many organizations had “shadow tenants”, unmonitored Oracle Cloud accounts, that were potentially affected by the breach.
The situation has raised concerns about Oracle’s transparency and incident response protocols. Critics argue that the company’s reluctance to acknowledge the breach publicly and its attempts to downplay the incident undermine trust in its services. As the threat actor continues to release sensitive information and threaten further disclosures, the pressure mounts on Oracle to provide clear and comprehensive communication regarding the breach and its impact on customers.
In an era where data security is paramount, Oracle’s handling of this incident serves as a cautionary tale about the importance of transparency and accountability in cybersecurity.










